PH cybercrime vulnerability among highest, says cybersecurity firm
MANILA, Philippines—What if you are trading on Binance Exchange, but access to your server is already being sold on the dark web, a hidden collective of internet websites that is accessible only through a specialized web browser?
As stressed by Kaspersky, a cybersecurity and digital privacy company, “demand for corporate and personal data on the black market is high, and it doesn’t always involve targeted attacks.”
The company said this as it revealed in its Digital Footprint Intelligence (DFI) report that 95 percent of all advertisements in the Asia-Pacific (APAC) region are the result of database leaks.
The DFI for APAC highlighted the results collected last year for organizations and countries to keep an eye on possible external threats and stay informed about potential cybercrime activities.
RELATED STORY: PH facing shortage of cybersecurity talent
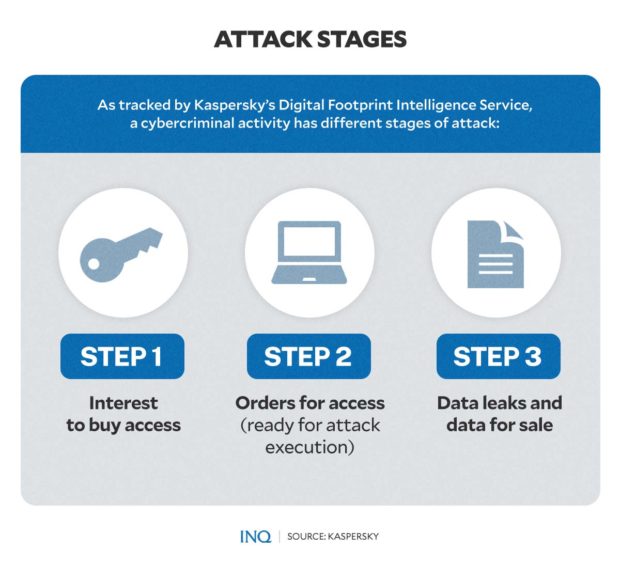
Article continues after this advertisementThis, as right now, cybercriminals prepare to attack, exchange data, and get money on the dark web. It said the examination of dark web resources provided insights into criminal activity through these stages of attack:
Article continues after this advertisementStage 1: Interest to buy access
Stage 2: Orders for access (ready for attack execution)
- Initial access brokers: Sell orders for specific organizations, or bulk orders with organizations grouped by industry and/or region.
- Insider activity sell orders: Request to sell insider services that can lead to credentials leak, source of information gathering service (e.g. PII data exfiltration by request), or data leak. The source is usually an insider’s broker.
- Malware logs: Credential stealing malware (stealers) collect credentials into resalable or otherwise accessible data with account usernames and passwords.
Stage 3: Data leaks and data for sale
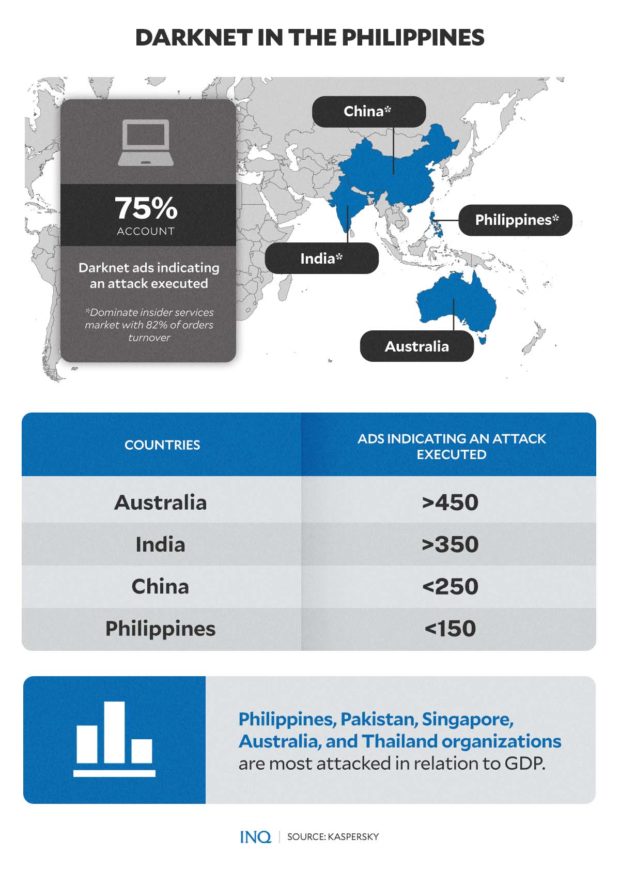
While Kaspersky stressed that data leaks in Singapore and Australia are by far the largest when looking at the weighted GDP amounts of orders, the Philippines has one of the highest count of dark web advertisements that are indicating an attack executed.
RELATED STORY: PH among least cybersecure in Asia, says study
An attack executed, it said, is the initial access broker activity on the dark web, which is an overlay network, where insiders sell access to a network, and malware logs with domain credentials.
“The most promising findings are from the attack execution stage: artifacts are stating that adversaries have capabilities or already have access to organizations’ networks or services, but there is no business impact yet,” Kaspersky said.
When it comes to advertisements on the dark web that are indicating an attack executed, the cybersecurity and digital privacy company said Australia, India, China and the Philippines account for 75 percent.
Australia has more than 450 advertisements indicating an attack executed
India has more than 350 advertisements indicating an attack executed
Mainland China has less than 250 advertisements indicating an attack executed
Philippines has less than 150 advertisements indicating an attack executed
Kaspersky stressed that the Philippines, Pakistan, Singapore, Australia, and Thailand are most attacked when weighed with GDP, while the Philippines, India, and China are dominating the insider services market with 82 percent of orders turnover.
RELATED STORY: Strengthening PH cybersecurity
Kaspersky said it should be noted that the Philippines, Pakistan, and Thailand were some of the adversaries’ interest to begin an attack or appeared as already compromised.
“Cybercriminal operations beneath the surface web are clearly busy. From attack preparation and execution, to the impact of a data leak and then selling and reselling of stolen information,” the company said.
Chris Connel, Kaspersky managing director for the region, stressed that “this functioning system is a serious threat for businesses and organizations here in APAC,” pointing out that selling data and access to the companies often goes hand in hand.
“This means a successful attack to (sic) your organization can be two pronged. Your confidential information can be stolen and be sold, and these cybercriminals can open and offer your infected system to more malicious coalitions,” he said.
High risk for PH
Dark web activity related to attack impact—advertisements on selling data leaks and compromised data—dominated the statistics as these are spread over time, where criminals sell, resell and repack a lot of data leaks from the past.
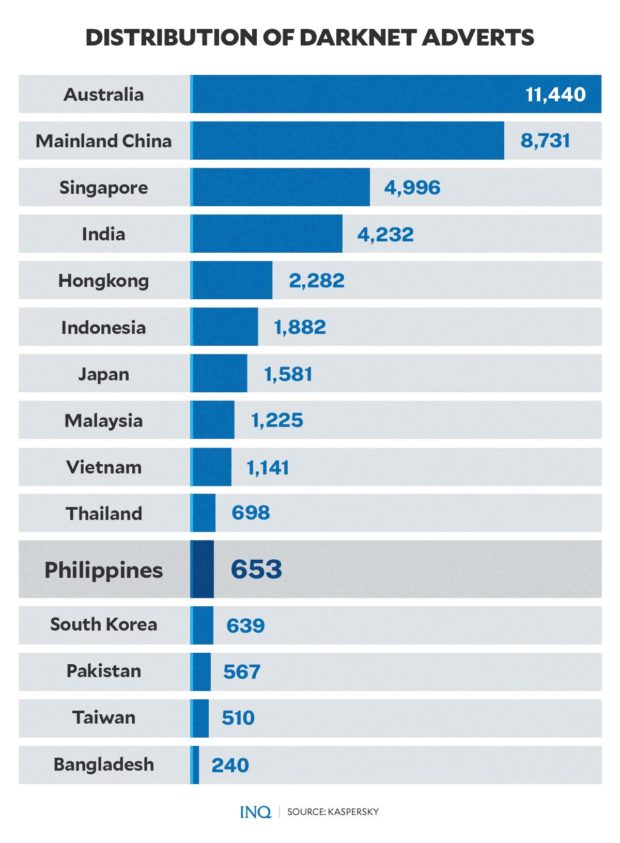
Based on data from Kaspersky, Australia (11,440), China (8,731), Singapore (4,996), India (4,232), Hong Kong (2,282), Indonesia (1,882), and Japan (1,581) have the highest share of dark web advertisements.
But while the Philippines only has 653 of these dark web advertisements, it is the most affected by ProxyShell—an attack chain that exploits vulnerabilities in Microsoft Exchange—with 28.6 percent of vulnerable services.
- Philippines: 28.6 percent
- Pakistan: 23.4 percent
- Malaysia: 21.7 percent
As for ProxyLogon, a vulnerability on Microsoft Exchange server that allows an attacker to bypass the authentication and impersonate as the admin, Japan is the most affected at 43 percent of vulnerable services.
- Japan: 43 percent
- Pakistan: 30.3 percent
- Philippines: 29.1 percent
Attack stages
Aside from the second stage, the cybersecurity and digital privacy company likewise highlighted the first and final attack stages in its DFI report—the interest to buy access, and data leaks and data for sale.
For the first attack stage, it said cybercriminals who are looking for initial access offers know that there is a large market for such advertisements.
“Organizations from Australia, India, mainland China, and Pakistan are the major adversaries’ interest to start an attack. These countries were present in 84% of ads from the attack preparation category.”
“Pakistan and Australia attract huge interest as seen by the number of orders weighted with their GDP. Looking at the size of infrastructure, businesses, and industrialization, mainland China poses relatively low interest for adversaries.”
This may indicate the presence of a language barrier cybercrime scene in the APAC region or the complications with network-level access to organizations in the country.
Access buy order is a request to buy access to a single or a list of specific organizations or industries in a specific region. Insider activity buy orders, however, are requests to buy insider services which can lead to credentials or data leaks, source of information gathering service.
The final attack stage indicates that once a data leak occurs, the sale or free access to the stolen information will follow. An indicator of compromise can be data leaks as well as insider activity orders.
Dark web data
As Kaspersky examined resources, it said there are two main types of data found when analyzing an organization’s digital footprint: fraudulent activities and cyberattack footprints.
Based on data, these are the amount of advertisements and fraudulent activities on the dark web for 2021:
- Cyber attack footprints: 40,819
- Fraudulent activities: 19,820
Kaspersky said there were 467 “attack preparation” advertisements or the buy order for access to the company’s resources published on the dark web.
There were 1,610 “attack executed” or the initial broker activity. This is divided into credential leaks from malware logs (674), access sell orders (649), and insider activity orders (287).
Kaspersky said there were 38,742 ‘attack impact’ or the sale of the company’s databases, sensitive documents.
Likewise, the fraudulent activities tracked by the company were credit card and withdrawal (5,865), document fraud service (5,415), SIM card orders (4,605), information gathering services (3,648), and insider activity orders (287).
Protection needed
Kaspersky stressed that attackers may gain access to the infrastructure of a random company to sell it to blackmailers or other advanced cybercriminals later.
“An attack like this can affect a company of any size, big or small, because corporate system access is often priced moderately on underground forums, especially compared to the potential damage to a business,” it said.
Sellers on the dark web most often offer remote access via RDP. To protect corporate infrastructure from attacks through remote access and control services, make sure the connection via this protocol is secure by:
providing access to services (for example, RDP) only through a VPN
using strong passwords and Network Level Authentication
using two-factor authentication for all services
monitoring for leaks of access data. Dark web monitoring is available on Kaspersky Threat Intelligence Portal
READ: Understanding digitalization: Why PH needs to do more
TSB