Jailing truth: Cyber attacks target dissent, anti-Duterte reports
MANILA, Philippines—A rights group in the Philippines sought to remember those killed in the Duterte administration’s bloody campaign against drugs and the crackdown on activists in what has been described as the “month of killings.”
Karapatan, a group which had been vilified by officials led by President Rodrigo Duterte himself, said it wanted to stand against the killings and bring messages of “hope, solidarity, and defiance” under a “regime who wants us to cower in fear and silence.”
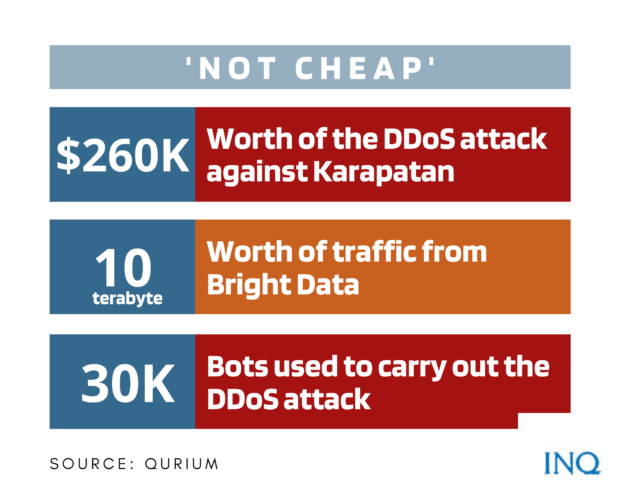
But as the group started to prepare for Aug. 17, the day that rights activist Zara Alvarez was murdered, its website came under online attack from July 21 to Aug. 20, which had cost an estimated $260,000.
READ: Cyberattacks on PH group traced
Qurium, a Sweden-based digital forensics group, said Karapatan was the target of a “sophisticated, well-resourced dedicated denial of service (DDoS) attacks.”
It stated that the attacks consisted of “application layer web floods,” a kind of DDoS that specifically targeted a part of karapatan.org which contains reports regarding killings in the Philippines.
CloudFare defines DDoS as a “malicious attempt to disrupt the normal traffic of a server by overwhelming it with a flood of internet traffic by using multiple compromised computer systems.”
The reports of killings posted on Karapatan’s website included those of Kian Lloyd delos Santos, Carl Arnaiz, Reynaldo de Guzman, Randall Echanis, the tribesmen in Panay Island and farmers in Negros Oriental and Negros Occidental.
In a previous statement, Karapatan Secretary General Cristina Palabay said the “cowardly attacks were obviously made to prevent the public from accessing our reports on the worsening state of human rights in the Philippines.”
In a report, “Israeli firm Bright Data (Luminati Networks) enabled the attacks against Karapatan,” Qurium said it reviewed the servers linked to a wave of DDoS attacks against the website that came from a proxy network operated by Bright Data in Netanya, Israel.
It said that from Aug. 10 to Aug. 20, 10 terabytes (enough for 250 movies) worth of traffic from Bright Data was recorded.
The attacks were carried out by 30,000 bots, over half of which were distributed in Russia, Ukraine, Indonesia and China.
“The traffic is far from cheap. One [gigabyte] of traffic ranges between $26-$35 for mobile proxies and $10-$15 for residential proxies,” the Qurium report said.
In a Rest of the World report, Bright Data said it has “absolutely no connection to the reported incident, and the Qurium report is categorically false, unprofessional, and unethical.”
While Bright Data denied that it was the source of the DDoS attack, Karapatan, since it was attacked online in 2018, “knows whose interests these attacks serve.”
Karapatan Public Information Officer Philip Jamilla said with the previous attacks, the deliberate targeting of Karapatan’s website, and the amount of money being thrown to lodge the attacks, “we can only guess the people behind them and the interests they serve.”
The Aug. 2021 DDoS is not the first instance that the website was attacked in an aim to take it down. In May to June 2021, Karapatan, Bulatlat.com, and Altermidya were targets.
READ: Media groups cry foul over ‘vicious cyberattacks’
Qurium said the websites were attacked with HTTP GET Flood, a kind of DDoS that had 350,000 hits in less than five minutes. Before the initiation of the DDoS, a statement on the call for the release of peasant activists Marcela Diaz and Virgilio Lincuna were posted.
Karapatan’s website was likewise attacked when it posted publications related to its submission of cases and recommendations to the Supreme Court regarding search warrants and fabricated cases against activists.
The attacks, Qurium said, were “one of the worst that they have seen in the last ten years that they have been checking attacks against civil society online spaces globally.”
Investigating the DDoS, Qurium said the attacks were traced to computer networks of the Department of Science and Technology (DOST) and the Philippine Army.
The internet protocol (IP) address of a machine was identified as 202.90.137.42 and was that it seemed to belong to the Philippine Research, Education, Government Information Network,” a unit of DOST’s Advanced Science and Technology Institute.”
READ: Probe pushed as DOST denies role in cyberattacks
Qurium said a unit in the same IP address was also registered to a certain “acepcionecjr@army.mil.ph” – part of the official domain and website of the Philippine Army.
The DOST, however, denied the allegation, saying that it is “unfounded and patently false.” Meanwhile, the Philippine Army said it respects freedom of expression and it “will never infringe on that freedom.”
READ: Cyberattacks on red-tagged news sites traced to DOST, Army
‘Sites rendered inaccessible’
The attacks on the websites of Karapatan, Bulatlat.com, and Altermidya, however, are not the only ones initiated against groups often vilified by the government—since 2018, DDoS were used to “silence dissent.”
Last Dec. 26, 2018, the websites of Bulatlat.com, Kodao Productions, and Pinoy Weekly – all part of the Altermidya Network – were attacked with DDoS that rendered their websites inaccessible for days.
After the publication of two reports—lowering the minimum age of criminal responsibility and peace consultant Rafael Baylosis’ release—last Jan. 19, 2019, the website of Bulatlat.com was attacked again.
The DDoS attack persisted and the website of Kodao Productions was also targeted on Jan. 25, 2019, taking it down for over a week.
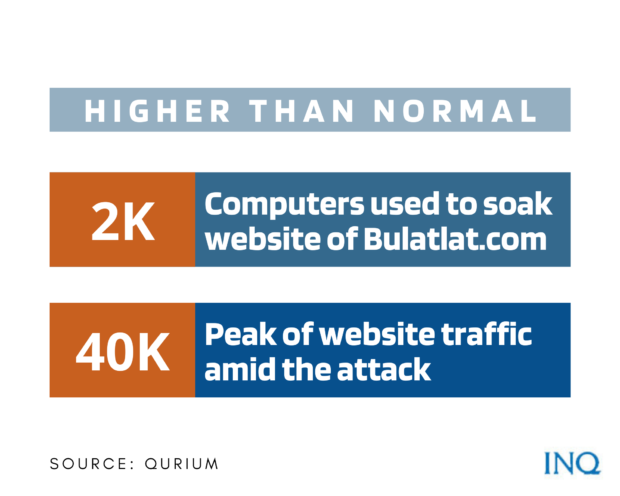
In an attack on Bulatlat.com, for instance, nearly 2,000 computers were used to soak the website with nuisance traffic and make it inaccessible, Qurium said, explaining that the traffic was 40,000 times higher than normal.
In the next attack, the one described as the “worst,” three million packets per second of bogus traffic were sent for an hour. This was likewise used to attack Kodao Productions. Qurium stated that the attacks required “extraordinary” resources.
A digital forensic report revealed those behind the attacks: IP Converge Data Services Inc. and Suniway Group of Companies. However, the two entities denied having direct knowledge of the said attacks.
On March 29, 2019, the Altermidya Network filed a civil complaint against the two companies at the Quezon City Regional Trial Court Branch 220.
Less than a year after the complaint was filed, the complainant Altermidya Network and defendants IP Converge Data Services Inc. and Suniway Group of Companies reached a compromise agreement following the defendants’ response that they have no knowledge of the attacks and that they commit to uphold the freedom of the press.
The complaint was collectively withdrawn, however, and Altermidya Network said that it will remain vigilant against attacks.
On Feb. 11, 2019, the website of the National Union of Journalists of the Philippines (NUJP) was the target of a DDoS attack which took it down twice.
The group said the DDoS was the same attack that took down the website two times on Feb. 8, 2019. This involved a total of 615 gigabyte of traffic, peaking at 468 gigabyte.
From Feb. 8 to Feb. 11, 2019, the NUJP had posts regarding detained media worker Frenchie Mae Cumpio, threats against a Surigao del Sur radioman, and Solicitor General Jose Calida’s harassment of ABS-CBN reporter Mike Navallo.
Its report stated that from 8 a.m. to 10 a.m. of Feb. 11, 2019, the website was hit with a 76-gigabyte DDoS attack and that after it was restored, a spike in access requests was recorded.
After initial investigation, it was found that the attackers’ most requested URL path is “https://nujp.org/?s=duterte,” the page that appears when the keyword “Duterte” is searched.
From April 12 to April 28, 2020, the websites of Baguio City-based Northern Dispatch and rights group Philippine Human Rights Information Center were likewise the targets of DDoS attacks.
In its report, Qurium stated that the groups were both reporting on “policy conflicts between local government initiatives and the effort of the national government to undermine decisions of local officials.”
A total of 6,000 compromised servers were involved in the attacks against the website of Northern Dispatch – nordis.net. Qurium said that the “botnet” originated in 106 nations with a large presence in Indonesia, India, Thailand, Brazil, US, China, Russia, and Ukraine.
The source of the attack also had access to a large amount of compromised machines in China and the Philippines where over 20 machines were used to soak the sites.
Kimberlie Quitasol, the editor-in-chief of Northern Dispatch, said in a Tawid interview that in less than 24 hours, access requests for the site reached 2.62 million with a data load of 39.60 gigabyte – statistics that are “way above the monthly average.”
‘No one else to blame’
Palabay said the “attacks only benefit those who want to silence us and our human rights work amid a pervasive state of impunity in the country.”
For Altermidya, the persistent attacks have the marks of a “well-oiled and well-funded machinery,” saying that clearly, it is not the “handiwork of a hacker acting alone.”
In 2017, a University of Oxford study said that around P10 million was spent to hire trolls to spread propaganda for Duterte and target his critics.
The study said that the President’s team of 400 to 500 cyber troops post pro-government comments and interact with dissenters through harassment, but Malacañang repeatedly denied involvement in the troll battalions.
READ: Attacks on PH alternative news websites worry media groups
“We believe that there is no one else that could possibly be behind these attacks than the Duterte regime itself, which has taken increasingly bold steps to curtail press freedom and the people’s right to know,” the Oxford study said.
Despite the attacks, Altermidya said it is committed to “report on the truths that need urgent telling.”
“We will not cow in the face of these attacks. Rather, it is our attackers who have much to fear, for our dedicated audience and the media community will not take this sitting down,” it said.